| AppleがiPhoneなど向けiOS 15.4とiPadOS 15.4をリリース! |
変更点はiPhone 12シリーズ以降で顔認証「Face ID」にてマスクを着用したまま認証できるようになるほか、新しい絵文字が追加されたり、SharePlayのセッションを対応アプリから直接開始できるオプションが追加されるなどし、iPadではユニバーサルコントロールによって1組のマウスとキーボードでiPadとMacの両方を操作可能になっています。その他、新機能追加および不具合修正、セキュリティー改善なども実施されているとのこと。
対象機種はiOS 15およびiPadOS 15の対象機種である「iPhone 13」シリーズや「iPad(第9世代)」および「iPad mini(第6世代)」を含むiPhone 6s以降およびiPod touch(第7世代)、iPad(第5世代)・iPad Air 2・iPad mini 4・iPad Pro以降の各製品にて無料で更新可能です。
その他、スマートウォッチ「Apple Watch」向け「watchOS」の最新バージョン「watchOS 8.5(19T242)」やスマートテレビ「Apple TV」向け「tvOS」の最新バージョン「tvOS 15.4(19L440)」、パソコン「Mac」向け「macOS」の最新バージョン「macOS 12.3(21E230)」なども提供開始されています。
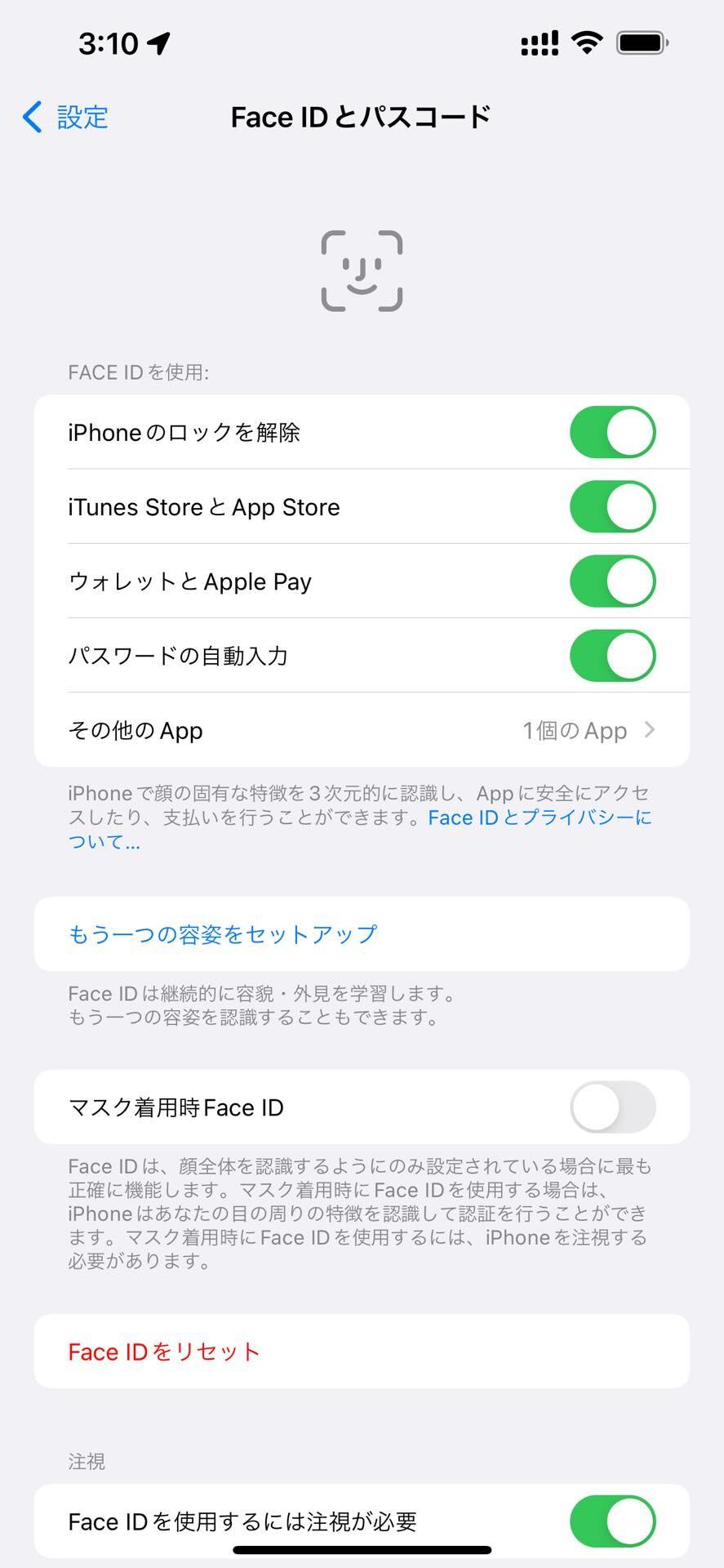
iPhone 12シリーズ以降の対応機種では更新直後にマスク着用時のFace IDの利用をするかどうかが確認されます。後で「設定」→「Face IDとパスコード」にて変更も可能iPhoneやiPod touch向けのiOS、iPad向けのiPadOSの最新メジャーバージョンとして現地時間9月20日に提供が開始されたiOS 15およびiPadOS 15ですが、その後、各種の新機能が追加されたiOS 15.1・iPadOS 15.1およびiOS 15.2・iPadOS 15.2、iOS 15.2・iPadOS 15.3が提供開始されていましたが、今回、新機能追加などが行われるiOS 15.4およびiPadOS 15.4が提供開始されました。Appleが案内しているアップデートの内容およびセキュリティーコンテンツの修正は以下の通り。更新は従来通り各製品本体のみでOTA(On-The-Air)によりダウンロードで行え、方法としては、「設定」→「一般」→「ソフトウェア・アップデート」から行えます。またiTunesをインストールしたWindowsおよびMacとUSB-Lightningケーブルで接続しても実施できます。
なお、単体でアップデートする場合のダウンロードサイズは手持ちのiPhone 13 Pro MaxでiOS 15.3.1からだと1.34GBとなっており、ファイルサイズは大きめとなっています。Appleが案内しているiOS 15.4およびiPadOS 15.4の更新内容と修正された脆弱性については以下の通りとなっています。
iOS 15.4iOS 15.4では、iPhone 12以降を対象に、マスクを着用したままFace IDでロックを解除できる機能が追加されます。このアップデートには、新しい絵文字のほか、SharePlayのセッションを対応Appから直接開始できるオプションが追加され、iPhone用のその他の機能およびバグ修正も含まれます。Face ID・iPhone 12以降で、マスクを着用したままFace IDを使用できるオプション・Apple Pay、およびSafariとApp内のパスワード自動入力で、マスクを着用したままFace IDを使用可能
絵文字・絵文字キーボードで、顔の表情、手のジェスチャー、調度品などの新しい絵文字を使用可能・握手の絵文字で、それぞれの手に別々のスキントーンを選択可能
FaceTime・SharePlayのセッションを対応Appから直接開始可能
Siri・iPhone XS、iPhone XR、iPhone 11以降では、オフラインの間もSiriが日付と時刻の情報を応答可能
ワクチン接種カード・“ヘルスケア”がEUデジタルCOVID証明書に対応し、新型コロナウイルス感染症(COVID-19)ワクチン接種、検査結果、および回復状況の検証可能な記録をダウンロードして保存可能・Appleウォレットの新型コロナウイルス感染症(COVID-19)ワクチン接種カードがEUデジタルCOVID証明書の書式に対応
このリリースにはiPhone用の以下の機能向上も含まれます:・SafariのWebページ翻訳機能がイタリア語と中国語(繁体字)に対応・Podcast Appにエピソードフィルタが追加され、シーズンや再生済み、未再生、保存済み、またはダウンロード済みのエピソードを絞り込み可能・iCloudのカスタムメールドメインを“設定”から管理可能・“ショートカット”が“リマインダー”とのタグの追加/削除/検索に対応・“緊急SOS”の設定をすべてのユーザを対象に“長押しして通報”を使用するように変更。“5回押して通報”は“緊急SOS”の設定のオプションとして今後も利用可能・“拡大鏡”のクローズアップ機能で、iPhone 13 ProとiPhone 13 Pro Maxの超広角カメラを使用して小さなものを見やすくすることが可能・“設定”で保存済みのパスワードに自分用のメモを追加可能
このリリースにはiPhone用のバグ修正も含まれます:・キーボードで入力した数字の間にピリオドが挿入される場合がある問題・写真とビデオがiCloud写真ライブラリに同期されない場合がある問題・“ブック” App内で“画面の読み上げ”のアクセシビリティ機能が予期せず終了する場合がある問題・コントロールセンターでライブリスニングをオフに切り替えてもオフにならないことがある問題・一部の機能は、地域やAppleデバイスによっては使用できない場合があります。Appleソフトウェア・アップデートのセキュリティコンテンツについては、以下のWebサイトをご覧ください:https://support.apple.com/ja-jp/HT201222
iPadOS 15.4iPadOS 15.4にはユニバーサルコントロールが追加され、1組のマウスとキーボードでiPadとMacの両方を操作できます。新しい絵文字のほか、SharePlayのセッションを対応Appから直接開始できるオプションが含まれます。このアップデートにはその他の新機能およびiPad用のバグ修正も含まれます。ユニバーサルコントロール・ユニバーサルコントロールにより、1組のマウスとキーボードでiPadとMacの両方を操作可能・テキスト入力はiPadまたはMacのどちらからでも可能、また両者間でファイルのドラッグ&ドロップが可能
絵文字・顔の表情、手のジェスチャー、調度品などの新しい絵文字・握手の絵文字で、それぞれの手に別々のスキントーンを選択可能
FaceTime・SharePlayのセッションを対応Appから直接開始可能
Siri・A12Z Bionic以降を搭載したiPad Proでは、オフラインの間もSiriが日付と時刻の情報を応答可能
このリリースにはiPad用の以下の機能向上も含まれます:・iPad(第5世代以降)、iPad mini(第4世代と第5世代)、iPad Air 2、iPad Air(第3世代と第4世代)、およびiPad Proで、音量コントロールをiPadの向きに合わせて調整されるように設定可能・iCloudのカスタムメールドメインを“設定”から管理可能・SafariのWebページ翻訳機能がイタリア語と中国語(繁体字)に対応・Podcast Appにエピソードフィルタが追加され、シーズンや再生済み、未再生、保存済み、またはダウンロード済みのエピソードを絞り込み可能・“ショートカット”が“リマインダー”のタグに対応。“ショートカット”を作成および編集するときにタグの追加/削除/検索が可能・セキュリティに関する勧告を非表示にすることが可能・“設定”で保存済みのパスワードに自分用のメモを追加可能
このリリースにはiPad用のバグ修正も含まれます:・キーボードで入力した数字の間にピリオドが挿入される場合がある問題・写真とビデオがiCloud写真ライブラリに同期されない場合がある問題・“ブック” App内で“画面の読み上げ”のアクセシビリティ機能が予期せず終了する場合がある問題・コントロールセンターでライブリスニングをオフに切り替えてもオフにならないことがある問題
一部の機能は、地域やAppleデバイスによっては使用できない場合があります。Appleソフトウェア・アップデートのセキュリティコンテンツについては、以下のWebサイトをご覧ください:https://support.apple.com/ja-jp/HT201222
iOS 15.4 and iPadOS 15.4- Accelerate FrameworkAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: Opening a maliciously crafted PDF file may lead to an unexpected application termination or arbitrary code executionDescription: A memory corruption issue was addressed with improved state management.CVE-2022-22633: an anonymous researcher- AppleAVDAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: Processing a maliciously crafted image may lead to heap corruptionDescription: A memory corruption issue was addressed with improved validation.CVE-2022-22666: Marc Schoenefeld, Dr. rer. nat.
-AVEVideoEncoderAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: A malicious application may be able to execute arbitrary code with kernel privilegesDescription: A buffer overflow was addressed with improved bounds checking.CVE-2022-22634: an anonymous researcher
- AVEVideoEncoderAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: An application may be able to gain elevated privilegesDescription: An out-of-bounds write issue was addressed with improved bounds checking.CVE-2022-22635: an anonymous researcher
- AVEVideoEncoderAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: An application may be able to execute arbitrary code with kernel privilegesDescription: An out-of-bounds write issue was addressed with improved bounds checking.CVE-2022-22636: an anonymous researcher
- CellularAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: A person with physical access may be able to view and modify the carrier account information and settings from the lock screenDescription: The GSMA authentication panel could be presented on the lock screen. The issue was resolved by requiring device unlock to interact with the GSMA authentication panel.CVE-2022-22652: Kağan Eğlence (linkedin.com/in/kaganeglence)
- CoreMediaAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: An app may be able to learn information about the current camera view before being granted camera accessDescription: An issue with app access to camera metadata was addressed with improved logic.CVE-2022-22598: Will Blaschko of Team Quasko
- FaceTimeAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: A user may be able to bypass the Emergency SOS passcode promptDescription: This issue was addressed with improved checks.CVE-2022-22642: Yicong Ding (@AntonioDing)
- FaceTimeAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: A user may send audio and video in a FaceTime call without knowing that they have done soDescription: This issue was addressed with improved checks.CVE-2022-22643: Sonali Luthar of the University of Virginia, Michael Liao of the University of Illinois at Urbana-Champaign, Rohan Pahwa of Rutgers University, and Bao Nguyen of the University of Florida
- GPU DriversAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: An application may be able to execute arbitrary code with kernel privilegesDescription: A use after free issue was addressed with improved memory management.CVE-2022-22667: Justin Sherman of the University of Maryland, Baltimore County
- ImageIOAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: Processing a maliciously crafted image may lead to arbitrary code executionDescription: An out-of-bounds read was addressed with improved input validation.CVE-2022-22611: Xingyu Jin of Google
- ImageIOAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: Processing a maliciously crafted image may lead to heap corruptionDescription: A memory consumption issue was addressed with improved memory handling.CVE-2022-22612: Xingyu Jin of Google
- IOGPUFamilyAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: An application may be able to gain elevated privilegesDescription: A use after free issue was addressed with improved memory management.CVE-2022-22641: Mohamed Ghannam (@_simo36)
- iTunesAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: A malicious website may be able to access information about the user and their devicesDescription: A logic issue was addressed with improved restrictions.CVE-2022-22653: Aymeric Chaib of CERT Banque de France
- KernelAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: An application may be able to execute arbitrary code with kernel privilegesDescription: A memory corruption issue was addressed with improved validation.CVE-2022-22596: an anonymous researcherCVE-2022-22640: sqrtpwn
- KernelAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: An application may be able to execute arbitrary code with kernel privilegesDescription: An out-of-bounds write issue was addressed with improved bounds checking.CVE-2022-22613: Alex, an anonymous researcher
- KernelAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: An application may be able to execute arbitrary code with kernel privilegesDescription: A use after free issue was addressed with improved memory management.CVE-2022-22614: an anonymous researcherCVE-2022-22615: an anonymous researcher
- KernelAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: A malicious application may be able to elevate privilegesDescription: A logic issue was addressed with improved state management.CVE-2022-22632: Keegan Saunders
- KernelAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: An attacker in a privileged position may be able to perform a denial of service attackDescription: A null pointer dereference was addressed with improved validation.CVE-2022-22638: derrek (@derrekr6)
- libarchiveAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: Multiple issues in libarchiveDescription: Multiple memory corruption issues existed in libarchive. These issues were addressed with improved input validation.CVE-2021-36976
- MarkupAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: A person with physical access to an iOS device may be able to see sensitive information via keyboard suggestionsDescription: This issue was addressed with improved checks.CVE-2022-22622: Ingyu Lim (@_kanarena)
- MediaRemoteAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: A malicious application may be able to identify what other applications a user has installedDescription: An access issue was addressed with improved access restrictions.CVE-2022-22670: Brandon Azad
- NetworkExtensionAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: An attacker in a privileged network position may be able to leak sensitive user informationDescription: A logic issue was addressed with improved state management.CVE-2022-22659: an anonymous researcher
- PhoneAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: A user may be able to bypass the Emergency SOS passcode promptDescription: This issue was addressed with improved checks.CVE-2022-22618: Yicong Ding (@AntonioDing)
- PreferencesAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: A malicious application may be able to read other applications' settingsDescription: The issue was addressed with additional permissions checks.CVE-2022-22609: Zhipeng Huo (@R3dF09) and Yuebin Sun (@yuebinsun2020) of Tencent Security Xuanwu Lab (xlab.tencent.com)
- SandboxAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: A malicious application may be able to bypass certain Privacy preferencesDescription: The issue was addressed with improved permissions logic.CVE-2022-22600: Sudhakar Muthumani of Primefort Private Limited, Khiem Tran
- SiriAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: A person with physical access to a device may be able to use Siri to obtain some location information from the lock screenDescription: A permissions issue was addressed with improved validation.CVE-2022-22599: Andrew Goldberg of the University of Texas at Austin, McCombs School of Business (linkedin.com/andrew-goldberg/)
- SoftwareUpdateAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: An application may be able to gain elevated privilegesDescription: A logic issue was addressed with improved state management.CVE-2022-22639: Mickey (@patch1t)
- UIKitAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: A person with physical access to an iOS device may be able to see sensitive information via keyboard suggestionsDescription: This issue was addressed with improved checks.CVE-2022-22621: Joey Hewitt
- VoiceOverAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: A person with physical access to an iOS device may be able to access photos from the lock screenDescription: An authentication issue was addressed with improved state management.CVE-2022-22671: videosdebarraquito
- WebKitAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: Processing maliciously crafted web content may disclose sensitive user informationDescription: A cookie management issue was addressed with improved state management.WebKit Bugzilla: 232748CVE-2022-22662: Prakash (@1lastBr3ath) of Threat Nix
- WebKitAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: Processing maliciously crafted web content may lead to code executionDescription: A memory corruption issue was addressed with improved state management.WebKit Bugzilla: 232812CVE-2022-22610: Quan Yin of Bigo Technology Live Client Team
- WebKitAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: Processing maliciously crafted web content may lead to arbitrary code executionDescription: A use after free issue was addressed with improved memory management.WebKit Bugzilla: 233172CVE-2022-22624: Kirin (@Pwnrin) of Tencent Security Xuanwu LabWebKit Bugzilla: 234147CVE-2022-22628: Kirin (@Pwnrin) of Tencent Security Xuanwu Lab
- WebKitAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: Processing maliciously crafted web content may lead to arbitrary code executionDescription: A buffer overflow issue was addressed with improved memory handling.WebKit Bugzilla: 234966CVE-2022-22629: Jeonghoon Shin at Theori working with Trend Micro Zero Day Initiative
- WebKitAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: A malicious website may cause unexpected cross-origin behaviorDescription: A logic issue was addressed with improved state management.WebKit Bugzilla: 235294CVE-2022-22637: Tom McKee of Google
- Wi-FiAvailable for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)Impact: A malicious application may be able to leak sensitive user informationDescription: A logic issue was addressed with improved restrictions.CVE-2022-22668: MrPhil17
記事執筆:memn0ck■関連リンク・エスマックス(S-MAX)・エスマックス(S-MAX) smaxjp on Twitter・S-MAX - Facebookページ・iOS 15 関連記事一覧 - S-MAX・iPadOS 15 関連記事一覧 - S-MAX・iOS 15 のアップデートについて - Apple サポート (日本)・iPadOS 15 のアップデートについて - Apple サポート (日本)・iOS 15.4 および iPadOS 15.4 のセキュリティコンテンツについて - Apple サポート (日本)・Apple セキュリティアップデート - Apple サポート